
Despite the clear, constant danger that weak passwords pose to an organization, many of them still try to solve this problem by implementing technology. The research identified problems and the need to urgently reduce the security risks posed by them. Too many organizations transfer responsibility for their management to employees and do not use automated password management technology that can help when things go downhill. Also, many organizations rely too much on manual management processes and have too much confidence that employees will apply the recommendations. The threat posed by human behavior combined with the lack of adequate technology exposes companies to the unnecessary risk of weak ones and passwords shared by employees. The focus of companies must be on solving both problems if they want to significantly raise the level of overall security. It can ruin your life. It sounds dramatic, but it’s true. If someone finds out your email or social network password, serious problems can arise and the situation can get worse, and worse, if the codes are for e-banking, it can empty your accounts.
Potential Cyber Attack Points

Even the most ordinary email account (or an account on a network service) that is no longer important to you can be worth an attacker. Based on the information from that account, a hacker can reveal passwords for other accounts (if you use the same or similar ones somewhere), and can also use the account to steal your identity and launch attacks on your family and friends. User awareness when it comes to passwords is generally still unsatisfactory. They are are the first line of defense against many internet diseases, but not enough people act accordingly.

Using your name in them (or any common name) is not a good idea. Also, hackers have a lot of success in discovering them that contain the names of celebrities, terms from pop culture and sports, and simple templates on the keyboard, because they know that people like to use combinations that are easy to remember. It remains a mystery why people, in addition to so many well-known cases of compromising data that are often written about, still do not pay attention to passwords and are unnecessarily exposed to risk from year to year.
Recommendations For Creating And Handling Passwords
- Use unique (do not use the same password for multiple sites and services).
- Use complex ones (minimum 10 characters, preferably 15, the combination of lowercase and uppercase letters, numbers, and special characters).
- It is important to remember them without writing them down, so use passwords that you can remember. If you have a lot of passwords and you are worried that you will not be able to remember everything, use one of the password manager tools, but be sure to choose a strong and complex master one that you will remember.
- Change them periodically (every 3-6 months).
- Use two-factor authentication wherever this option exists.
- Always log out of devices that are used by more people.
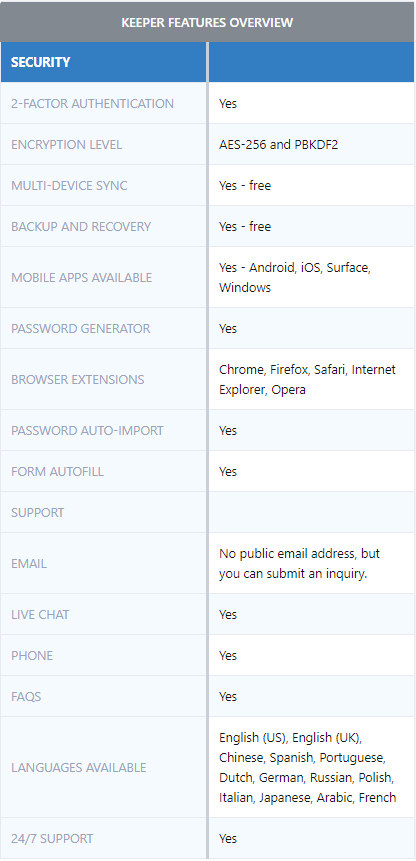
When it comes to storing important data such as passwords, prefer to store them locally, in an encrypted file (with the ability to transfer to other devices), without extensions in the browser here and there there are vulnerabilities). Keeper Password Manager & Digital Vault is one of the most famous freeware programs with open-source software. They are stored in an encrypted database, you can work with several such databases, you can transfer it to any other device. Their storage is organized in the structure of the tree (its sections can be changed), and the fields Name, Password, Link, and Comment are available when saving the password, where you can describe in detail what this refers to – everything is convenient and simple enough. This security tool has lots of reviews, check this page to find out more. They store all our data and are protected by one master password or some other form of authentication. When you need to log in somewhere, your manager will do it for you. So it’s faster, more comfortable, and safer. Synchronization with other devices is possible. In that case, you only need to enter the login password and the mail address to start the synchronization.
Choosing a master one

- Use a suggestion. A funny line or saying will be a great background for your password.
- Uppercase and lowercase letters. Correct spelling – rather a lack of a password.
- Embed special characters. You can add several special characters.
- Dual Authentication Be sure to use two-factor authentication to further protect access to the manager.
With a few exceptions, unfortunately, there is no way to permanently delete content posted online. Even if you remove the original post, you can’t be sure that others haven’t made copies or shared your content on other networks. Don’t put on the net what you wouldn’t want others to see.
A tried and tested tactic of cybercriminals is to trick you into downloading malicious software that allows them to steal information. From a popular game to an email that offers technical support, malware can be disguised in many different ways.
Avoid downloading apps that look weird or come from an unknown site. Not sure if the email is authentic? Ask yourself the following questions: Does the sender have a strange email address? Is the greeting impersonal? Are there a lot of spelling mistakes? Is there an unusual sense of urgency?

If you do not update your defense, cybercriminals will sooner or later find a way to overcome it. Be sure to follow and download the latest updates to your operating system and make an extra effort to check the privacy settings in the applications and browser you use.
When you connect to the Internet through a public connection, such as Wi-Fi in a mall, you have no direct control over its security. If you are unable to establish a secure connection or ensure that your device is protected, do not share sensitive information. It’s better to wait until you get home and make sure you’re using a secure Wi-Fi network.
Never hastily click on a link or post. Nothing is more important than your online security. Navigating safely through online threats can be stressful, but many resources can help you. Whenever you find yourself in a situation where you are unsure or suspicious, always rely on the expertise of those you trust – whether they are friends, a parent, a teacher, or even a technology partner.




